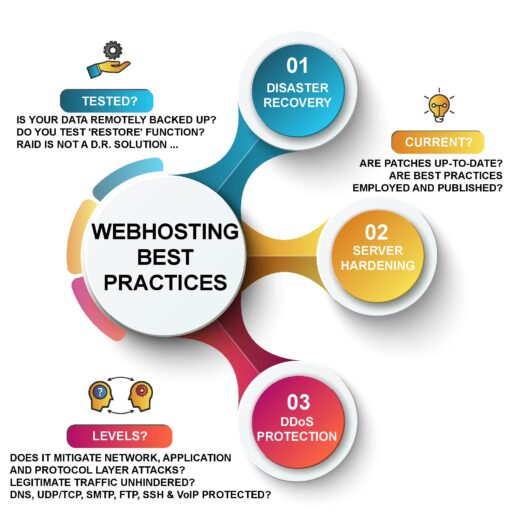
When web hosting providers start asking about hardware DDoS protection that cost upward of $32,000 and licenses running $10,000 plus, you know that security is a serious issue, especially in today’s world of cybercriminal attacks.
When web hosting providers start asking about hardware DDoS protection that cost upward of $32,000 and licenses running $10,000 plus, you know that security is a serious issue, especially in today’s world of cybercriminal attacks.
Considering that some of these firewalls only protect you for attacks under 50Gbps, the real cost to protect yourself against attacks ten times that magnitude is staggering.
Before you even get to that level of security though, your servers themselves need to be locked down. There are a number of ways to do that – we’ll address a few of the more applicable methods here:
Use SSH Keys
The latest controversy between the FBI and Apple centered around unlocking an iPhone that utilized encryption. In this scenario, SSH keys utilize cryptographic keys using private and public key pairs for authentication. This prevents password based login brute force attacks whereby a malicious user can repeatedly attempt to gain access to your server.
This is comparable to using an exceptionally strong username – password combination, so much so that it’s virtually uncrackable – or at the very least, not worth attempting.
To some, setting up any type of cryptologic key seems taunting, but it really isn’t. The entire process can be completed in a few minutes.
Setup Firewalls
I once sold a firewall device to a local firm for $5000 and thought that was a fortune to pay for protection. Today, this seems like a pittance compared to yesterday’s outlay for security. Essentially, firewalls can be software or hardware based, and as designed are engineered to block or restrict access to everything except what’s absolutely publicly necessary.
Internal services can be rendered completely inaccessible to the public, and any ports not being utilized can be blocked entirely (in most configurations).
Firewalls essentially provide you with an extra layer of security, to protect those components of your server that are vulnerable to exploitation.
Some firewalls are more difficult than others to set up, but once done normally only need to be tweaked. As an alternate, you can always resort to iptables or a CSF firewall.
Setup a Virtual Private Network (VPN)
VPN’s have been around for a number of years. The first time I set one up was to securely login to the corporate intranet from my home personal computer. They’re an encrypted tunnel between two end points, offering one way to connect to a remote server over a secure connection.
To make this work, the server has to be configured so that your applications and firewall allow the use of this type of funnel. Is the installation process difficult? Well, it’s not entirely simple, but once setup it’s very much worth the effort.
SSL/TLS Encryption
SSL certificates are used to authenticate different entities to one another, normally an end user with an online ecommerce store or banking institution.
These basically prevent hacking attacks where a cybercriminal imitates a server in your network to intercept traffic.
Google recently stated that it was pushing for all websites to be SSL enabled, which we also recommend as it added an additional layer of security.
Performing audits on your server
Basically, by performing an audit on your server, you discover the services that are running on it. Doing so enables you to understand where attacks may occur, allowing you to proactively lock them down. Obviously, the more services you have running, the greater the odds that there exists some vulnerability on your network.
While performing audits is recommended, do you have a protocol in place to receive security alerts associated with vulnerabilities on the services running on your servers?

BROUGHT TO YOU BY PROLIMEHOST
We’ve been in the web hosting industry for over a decade, helping hundreds of clients succeed in what they do best and that’s running their business. We specialize in Virtual Private Servers (VPS) and dedicated servers, with data centers in Los Angeles, Denver & Singapore.
VPS SERVICES: LIGHTNING FAST SSD VIRTUAL SERVERS
Our Virtual Private Servers all feature high performance Xeon processors and SSD storage in a RAID10 configuration to optimize your server’s performance, which dramatically enhances visitor experiences on your site.
That speed is backed by unparalleled 24/7 support, featuring both outstanding response AND resolution times to maximize your uptime.
Now is the time to join the ProlimeHost virtual private server revolution.
DEDICATED SERVERS: BACKED BY A 99.9% SLA NETWORK UPTIME GUARANTEE
We only use enterprise-class hardware in our dedicated servers and offer a four (4) hour hardware replacement. Throw in IPMI for remote management, support for public and private networks, free operating system (OS) re-installs, and SATA, SAS & SSD (including NVMe) storage. Call 1-877-477-9454 or contact us. For everything from gaming, AMD and GPU servers to cheap dedicated servers, we’re here to help.
ASIA OPTIMIZED SERVERS: IMPROVING CONNECTION SPEED AND QUALITY
Procuring an Asia optimized server improves the connection speed and quality between the server and the users in Asia or China. This can reduce latency, packet loss, jitter, and bandwidth issues that can affect the performance and reliability of the server and the applications hosted on it. For more information, please call 1-877-477-9454 or contact us.